Archiving self-destructing Gmail messages with Firefox
N.b. while the methods described in this post were all tested to work as of the date posted, Google may find ways to prevent these methods working in the future, especially considering W3C’s move towards standardising DRM within web browsers.
Recently, Google has been pushing users onto the new Gmail redesign, which will soon roll out to everyone like it or not. The most interesting new feature of the redesign is the so-called “confidential mode” which allows users to send self-destructing emails. Google hosts the contents of the “email” as a webpage on their own server, and just emails the link. After the expiration date, or at the whim of the sender, Google refuses access to the main content, although the (dead) link stays in the receiver’s inbox, and the full email remains in the sender’s outbox.
This article is written under the assumption that the sender is using the new-Gmail, but you, the receiver, are using an external email provider. If you are both on the new-Gmail, then the Gmail web app presents confidential emails to look like a regular email when in fact the email body is just a link to external content. In this case you will need to use the “show original” option in Gmail to reveal the raw email and extract the link to confidential-mail.google.com/… so you can follow the instructions in this post.
Furthermore, Google claims to use “built-in Information Rights Management (IRM)” to “remove the option to forward, copy, download or print messages” in order to “reduce the risk of confidential information being accidentally shared with the wrong people.” (In other words, JavaScript and CSS that attempts to prevent the user’s browser from letting them copy the hosted email text)
However, there are concerns that the self-destruct feature could potentially be abused as a means to destroy evidence by governments, and companies facing litigation.
So, is someone using Gmail confidential mode to make a business deal you know they’ll be “unable to recall” later? Or perhaps they have revealed that your wildest conspiracy theories are true, but plan to deny all knowledge after the message expires just because they like to mess with your mind. What do you do?
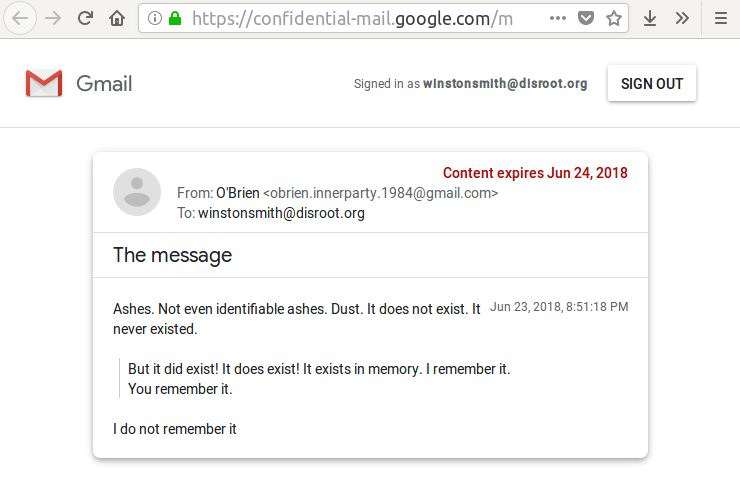
1. Screenshots ✓
The most obvious workaround is to take a screenshot, or if all else fails, physically take a photo of the screen. Coincidentally, Firefox has a convenient screenshot tool built into the browser itself.
2. Downloading ✓
While Google doesn’t provide a download button, your web browser does! Menu > Save Page as > Web Page complete. The text of the message will be captured in the downloaded HTML itself, so your local copy will never expire.
3. Printing ✓
Nothing like having a hard-copy for peace of mind. But if you attempt to print the page, all you will see is “printing is not allowed by the sender of this message.” This is due to abuse of @media print CSS rules to hide the main content when printing. The Style Editor tab of the Firefox Web Console (Menu > Web Developer > Web Console) makes it easy to comment these out. Alternatively, click the eye-shaped icon on the left to disable the CSS style sheet completely.
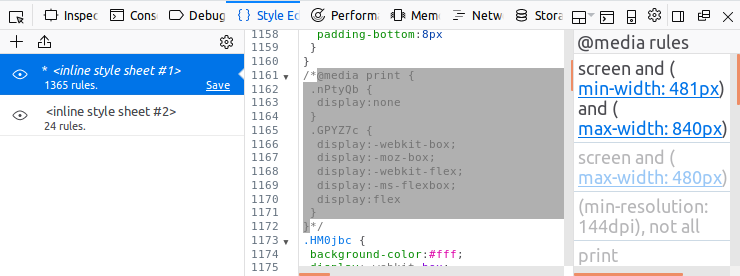
I also tried to do this in Google Chrome, but it doesn’t seem to provide an easy way to edit @media rules in the same manner Firefox does (send me a screenshot if you find a way).
4. Copy-pasting✓
Google uses two tricks to prevent copy-pasting text, so you will need to bypass both of them.
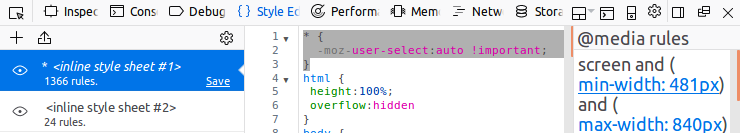
Firstly, they are using the CSS user-select property to prevent you from selecting text. You can set this back to defaults by writing a custom rule to override it like I did in the screenshot below, or just disable all CSS (similar to what we covered in the Printing section).
Secondly, they are using JavaScript to block the context menu that lets you use copy text. You can disable this by typing about:config into the address bar and setting dom.event.contextmenu.enabled to false (the name is a bit misleading, but false means that JavaScript doesn’t have the ability to block the context menu).
5. Forwarding ✗
To prevent people from forwarding the link, Google requires that to access the content users either have to log-in with their Google account (if they associated one with their email address), or enter a verification code sent to their email/phone.
To be clear, you can forward the link itself, but no-one will be able to see the main content unless they are signed in as you. If you are using Gmail or associated your email with a Google Apps account, you would need to give them your Google account details (bad!). If you are using an email provider not associated with Google (which I’ll assume from this point on), you would need to near-instantly let whomever you forward the “confidential” email to know any verification codes Google sends to your email/phone.
Of course, you could take a screenshot, download the content, print to a PDF, or copy-paste the text and per above and send that in an email instead.
Non-repudiation
The real problem with these techniques is that screenshots, HTML, PDF, and text can all be easily faked. They are okay as tools to assist your memory, but don’t offer any verifiable proof.
Initially, I considered using Wireshark to capture a full TCP dump, along with getting Firefox to output the ephemeral encryption keys it uses, so that an eternal party can decrypt the dump and audit that the traffic, including the HTTPS certificates (Jim Shaver has a nice guide on this if you’re curious).
Unfortunately however, HTTPS does not offer non-repudiation. All it would take is a small modification to the protocol, such as TLS-N, to allow the client to request a digital signature at the end of the communication. But alas, in current protocols, after a short TLS handshake that verifies to the client that the server is who they say they are, all traffic is encrypted using a symmetric key known to both the client and server. It prevents others from snooping, but both the client and server have all the information required to write a fake log that seems legitimate. In short, even if you capture all your network traffic, it’s no more trustworthy than a screenshot.
Gmail’s lack of a proper signing mechanism leaves only one option if you want anyone to believe that your screenshots are real: if you receive a “confidential” self-destructing message from Gmail, show as many friends and colleagues as possible before it expires!
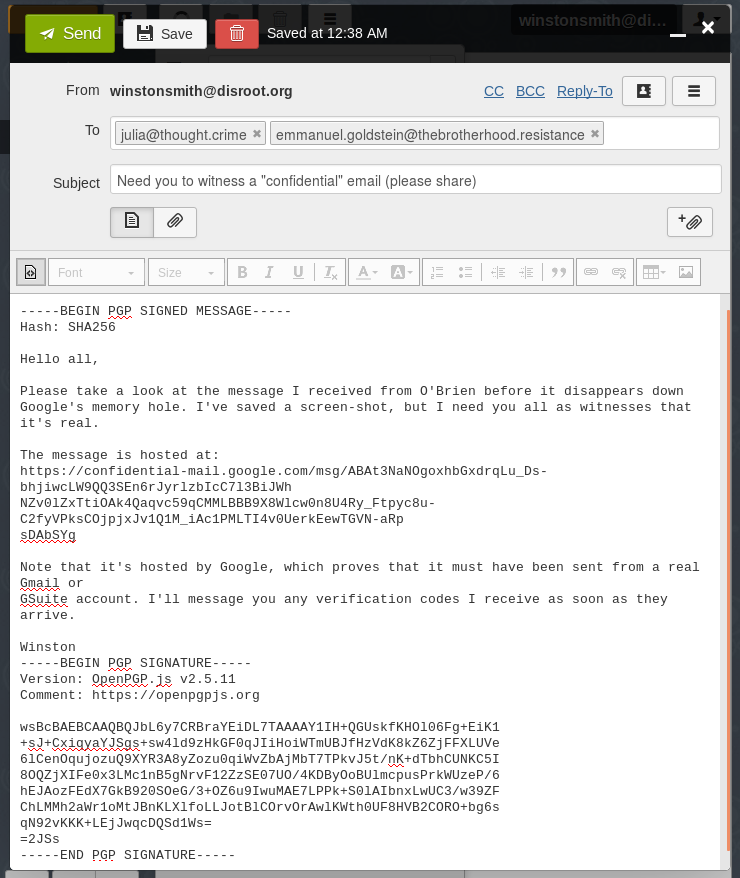
(What’s that “PGP SIGNED MESSAGE” stuff about? That’s OpenPGP, a way to cryptographically sign and encrypt messages to get real confidentiality. Unlike Gmail, it offers non-repudiable evidence that it is really Winston (or someone with access to his private key) who sent the message. It also allows (optionally) encrypting the message with the receiver’s public key so that no-one—be it Big Brother, Google, or the NSA—can read the message as it passes through transit.)
Lawyer Up
Depending on the circumstances, there may be other non-technical solutions to obtain evidence. Thanks to the folks at the Reddit r/privacy sub for sharing their suggestions on this:
- Create a “reverse paper trail”: write back to the sender documenting what they sent you, asking them to confirm that they sent it and make clear to them that failure to reply will be taken as implicit acknowledgement.
- Tell the sender you were unable to open the link because you were concerned that it could be a phishing attempt, and ask them to resend the content in a regular email.
If the content is still stored on Google’s servers, even if inaccessible, Google could potentially retrieve the email or verify your screenshot if a court were to order them to do so. Of course, that’s only possible if Google are keeping the original messages, and it’s unclear whether or not they do:
- A copy will stay in the senders outbox, until they delete it and empty their trash.
- For businesses using G Suite, the business can (optionally) retain a copy of all outgoing mail (including confidential email) originating from within the business (hopefully government organisations would have this enabled so they can follow up if they have a rouge employee that uses it to harass people).
- Even after the email has expired and been deleted by the sender and business (if any), it’s possible that the content still remains on Google’s servers, but how long is unclear:
- For regular emails, even after deleting the email and emptying the trash, Google maintains their own offline backup that could last “up to 60 days.”
- Mashable speculated that the “wording seems to specifically skirt the question of whether emails remain on Google’s servers”, Google’s official response was that “we’re not able to comment on internal procedures.”
- Business Insider says that confidential emails “are never truly destroyed”, quoting Google’s official position as being “received messages in confidential mode do not ‘explode,’ ‘self-destruct,’ ‘vanish,’ or “disappear.’” However, this was in the context of G Suite, and it may simply have meant that the responsibility is left to the business using G Suite to decide whether to accept incoming confidential emails and configure how long their outgoing emails are retained.
- BBC suggested that confidential mode was released to help businesses be “GDPR-compliant.” Google’s GDPR policy for G Suite states that “Google will delete the relevant customer data from all of its systems within a maximum period of 180 days unless retention obligations apply.”
(Please note that I’m a software engineering research student, not a lawyer, so please seek legal advice in serious cases)